Artificial Inteligence
CYBERSECURITY
Protect your Business from Viruses and Hackers with the Best Cybersecurity Company
Customizable Cybersecurity Plans
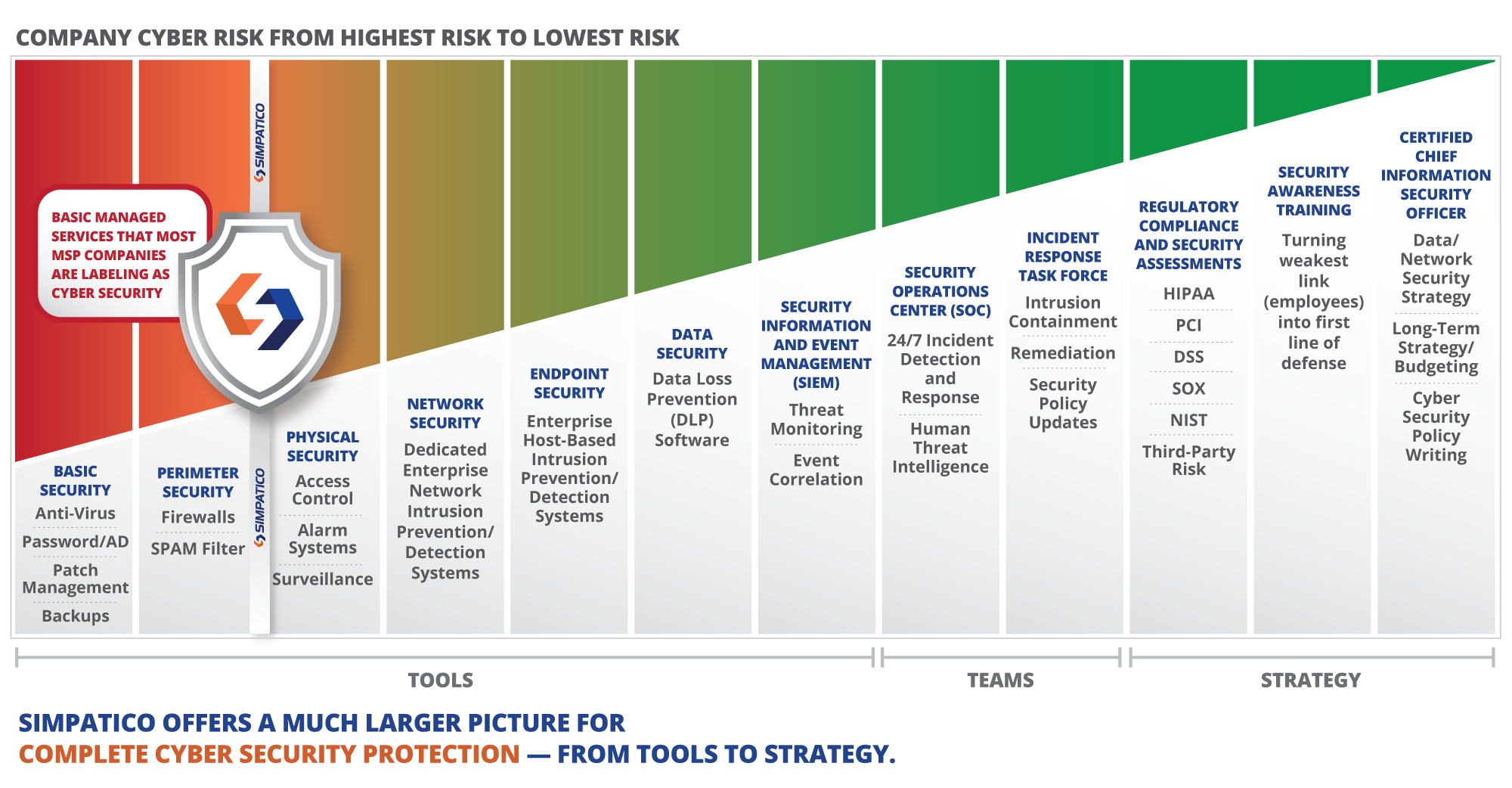
We offer highly-customizable cybersecurity solutions to protect the balance sheet and value of your company. Whether you are looking for basic security services to reduce risk, compliance consulting, or a top-down organization-wide security architecture, Simpatico has your ideal package. Our Cybersecurity services provide multiple layers of security guarded by our artificial intelligence engine that works automatically, twenty-four hours a day. Our cybersecurity portfolio comes with disaster recovery solutions to protect you against paying ransomware and bring you back safely from a hacking attack.
CYBERSECURITY SERVICES
Learn more about our Cybersecurity Services for Your Business or Organization today.
Advanced DNS Security Filtering
Installed Agent or DNS lookup Change
- It allows organizations to proactively improve Internet security by blocking access to malicious URLs that host phishing forms or are used to distribute malware.
- Prevent employees from visiting websites that may compromise network security.
- Infected systems are limited in wreaking additional havoc.
- Phishing and Malware protection
Endpoint Detection and Response
(EDR) & Remediation Installed Agent
- Protects computer hardware devices against hacking attempts and stealing of user data.
- Responding to threats in real-time, increasing visibility and transparency of user data, detecting endpoint events and malware injections, creating blacklists and whitelists.
- 24/7/365 Security Operations Center (SOC) staffed by teams of highly trained specialists using AI-driven tools that no SMB can afford or operate on their own.
- MSPs typically bolt-on EDR solutions based on a budget so the effectiveness of the EDR solution is weak (false positives, not enough manpower to manage all the data, etc.).
- World-class solutions are now highly affordable as progressive MSSPs expand the availability.
24/7 Monitoring
Web-based Service
- 24/7/365 Security Operations Center (SOC) staffed by teams of highly trained specialists using AI-driven tools that no SMB can afford or operate on their own.
- Our security analysts continuously monitor threat dashboards to catch advanced cyber-attacks, sifting through data from network flows, endpoint sensors, & other security logs.
- Cybersecurity threats don’t sleep. Neither should your network monitoring.
Dark Web Monitoring
Web-based Service
- It provides insight into leaked or breached data and employee behavior which could be the vector into your business.
- Improved governance, policies to restrict risky user behavior, enforced password policy and management
Security Operations Center (SOC)
Attack Detection
- Incident detection and response are the most challenging stages of the cyber security incident cycle. Organizations can sometimes take years to realize a breach occurred. With Simpatico’s dedicated SOC, DT Engineering will be able to get near-real-time attack detection.
Cyber Awareness Training
Web-based Service
- A formal process for educating employees about computer security, corporate policies, and procedures for working with information technology
- A downward trend in the number of incidents over time. Valuable insight into present-day threats and trends
- Develop strong internal company policies around high-risk processes
- Builds a security culture into your business
Cybersecurity insurance is an essential part of any modern business strategy. However, meeting the insurance requirements can be a complex process. As an experienced MSP, we can streamline this process, ensuring that you meet and exceed these requirements while
simultaneously improving your overall cybersecurity posture.
Contact us today to find out more about how we can help you navigate the audit process for your cybersecurity insurance. Protecting your digital assets has never been more critical; let us help you do it right.